Cyber Security Assessment
What is a Cyber Security Assessment?
Cyber security assessment is comprised of a comprehensive analysis of your IT environment to establish your vulnerabilities, assess your risks and determine your general preparedness to cyber threats. Such evaluations give companies a clear picture of their present security positions and which areas they should improve. A cyber security assessment, unlike a regular check-up, delves into your IT infrastructure, policies and practices such that when a check-up is conducted, it is thorough.

Why Do You Need a Cyber Security Assessment?
All organizations, both small and large, can be targets of cyberattacks. A cybersecurity assessment can enable you to find the gaps before malefactors penetrate. Lack of frequent reviews leaves businesses at risk of blind-side weaknesses. Moreover, evaluation supports the industry’s best requirements and regulatory compliance, which decreases the risk of monetary immediate income, lawsuits, and career-ending reputations.
Cyber Resilience Assessment: Strengthening Beyond Defense
Unlike traditional assessments which concentrate on vulnerability identification, a cyber resilience assessment determines how your organization can respond, adapt to the situation, and speedily recover after a cyberattack. Cyber resilience is more than just prevention; it also guarantees continuity, minimal impact, and quick recovery of services after incidents happen. Organizations that do not forgo cyber resilience are not afraid of threats because they are confident to tackle any threat and recover in the shortest time.
How to Perform a Cyber Security Assessment?
Performing a comprehensive IT security assessment involves clearly defined steps. First, identify the scope and objectives of the assessment, outlining which aspect of your IT environment you are going to examine. Then, collect information by reviewing your security laws, network, and working practices. Engage your IT and security team to analyze and discover existing safeguards and breaches.
Compare the security practices in your company with industry best practices, standards, and requirements. Once you have documented your findings, prepare an action plan that defines the steps necessary to address the weaknesses you discovered. Finally, keep a record of your improvements and monitor your results regularly to maintain security and address new threats.
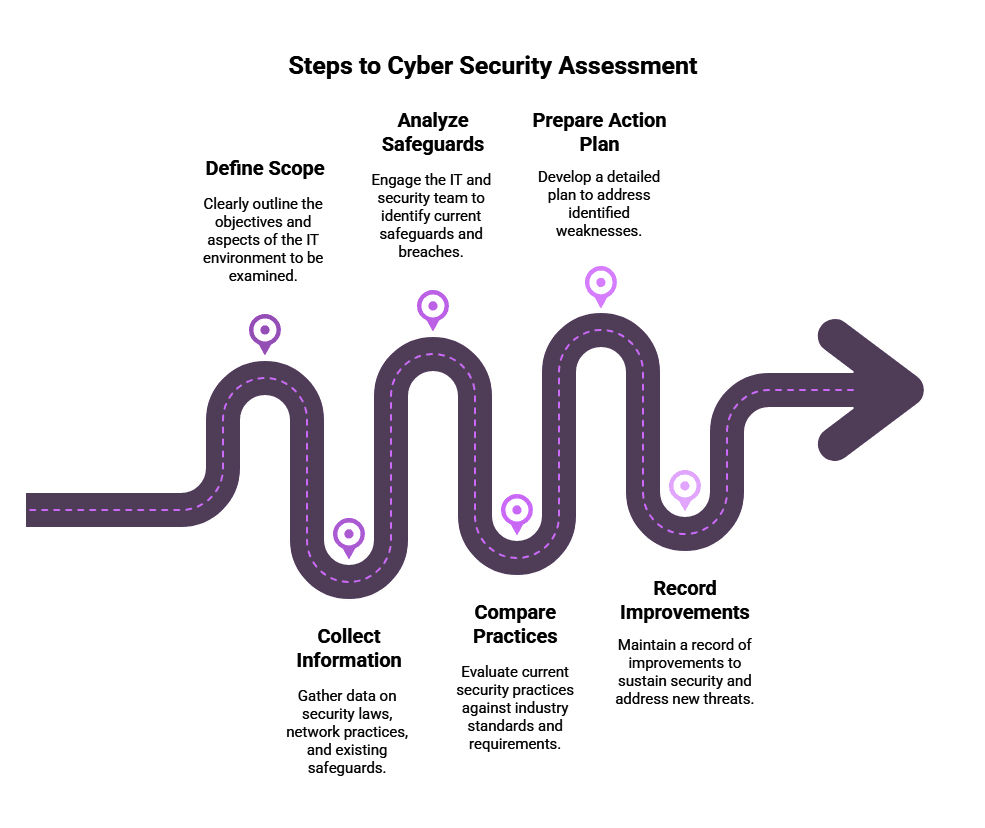
What's Included in a CyberSecurity Assessment?
A detailed cyber security audit investigates a number of key aspects of your company. This comprises the assessment of your endpoints, networks, and servers. It examines access control by users, data encryption, firewalls, and software updates.
Assessments also examine your policies around incident response, employee cybersecurity awareness, and compliance with regulatory standards. In short, they offer a comprehensive look into your entire cybersecurity ecosystem.
Cyber Security Assessment for Businesses: Protecting Every Size
Frequent evaluations are beneficial to businesses, large or small. Comprehensive and continuous assessments may be performed in large enterprises as they have more complicated IT infrastructures and an increased exposure to risk. Frequent assessments are also required by small businesses and medium businesses, but they may deploy free cybersecurity assessments first to get a clear picture of their security baseline. Assessments enable all businesses to have powerful safeguards and healthy cyber resiliency, no matter the size.
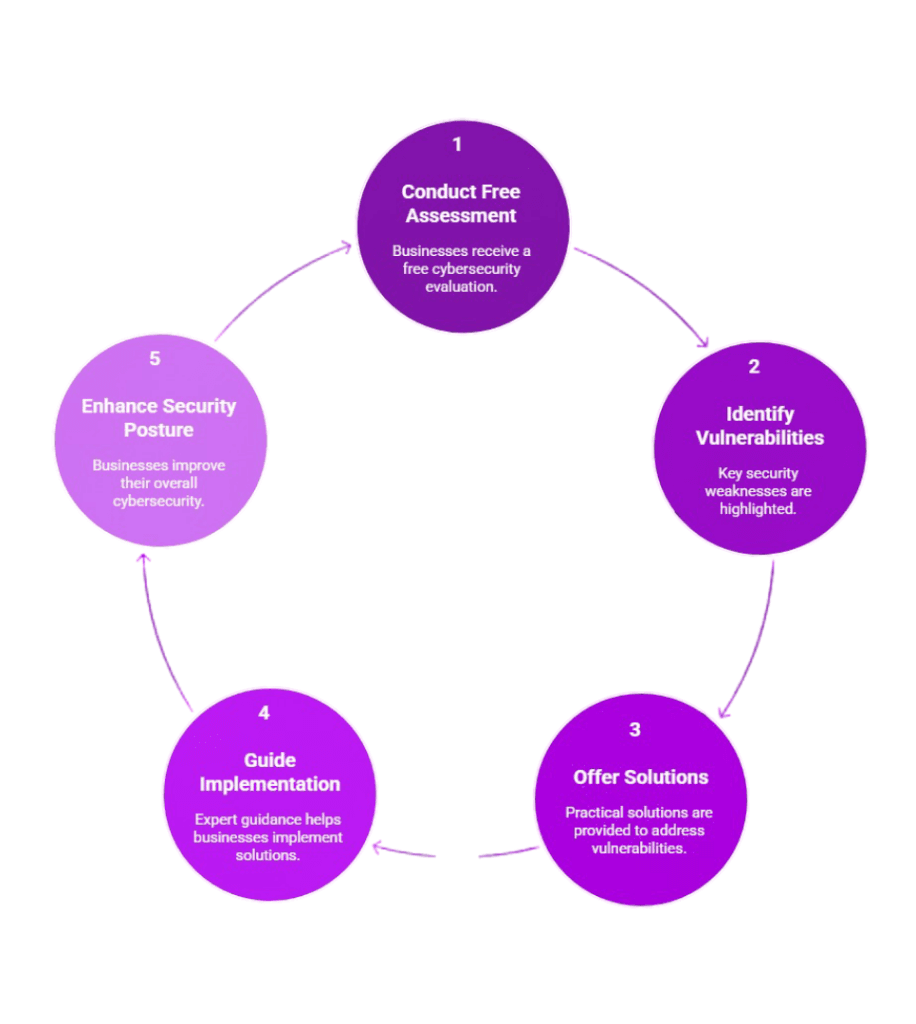
Free Cyber Security Assessment for Businesses
At Hoploninfosec, we believe every organization deserves strong cybersecurity, regardless of its budget. This is why we provide a free cybersecurity assessment to businesses that want to know their security posture without parting with money instantly.
This diagnostic test highlights the most serious areas of vulnerability and severe threats, offering concise, workable solutions to start enhancing your security. Although it cannot replace a comprehensive assessment, it provides small and growing businesses with the needed information for their future course of action.
We aim to popularize cybersecurity. Hoploninfosec is not just a report but the foundation of long-term protection because, through this free assessment, you will get guidance from our team who care about the safety and resilience of your organization.
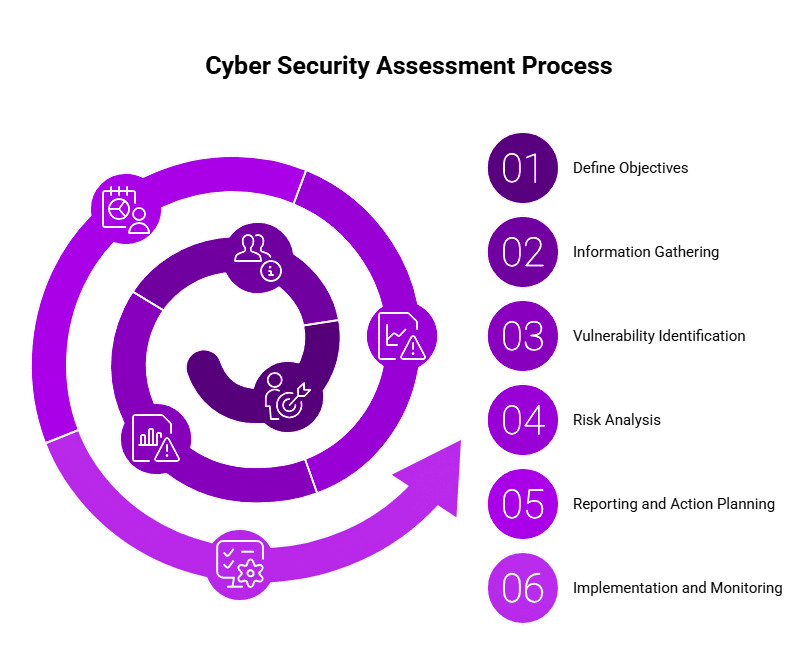
Steps Involved in Cyber Security Assessment
An effective assessment should be described by a systematic process:
- Define Objectives: Clearly establish what areas of cybersecurity you want to evaluate.
- Information Gathering: Collect details about your current security policies, procedures, systems, and infrastructure.
- Vulnerability Identification: Make use of special cybersecurity tools to identify hidden vulnerabilities.
- Risk Analysis: Assess the duration and consequences of the impact of the vulnerabilities identified as probable to be exploited.
- Reporting and Action Planning: Clearly document findings and provide actionable recommendations to strengthen defenses.
- Implementation and Monitoring: Implement the recommended improvements and continuously monitor progress.
Cyber Security Risk Assessment and Management
Cybersecurity risk estimation evaluates a certain threat to your organization, its forecasted effect, and probability. Risk management involves making knowledgeable choices on how to deal with the dangers. The major distinction between risk assessment and cybersecurity assessment is the approach that addresses risks and their possible effect specifically, and presents a general study that answers system settings, policies, and compliance necessities.
How to Evaluate Cyber Security Risks in Your Company
Evaluating cybersecurity risks begins with identifying critical assets, such as sensitive customer data, intellectual property, or vital business systems. Once these assets are identified, threats, weaknesses, and possible effects in the case of breaches can be determined. Depending on their probability and impact, assign levels of risks so that your business can prioritize future actions. Routine assessment assists your company in anticipating incoming threats and creating a strong defense system.
Importance of Cyber Security Assessment for Business Continuity
Financial losses are another significant effect of cybersecurity incidents, which can badly affect operations, disrupting trust. Cybersecurity tests are regular checks to monitor weaknesses and thus prevent losses in the event of a shutdown or attack. Organizations, which perform frequent assessments of the state of their cybersecurity, have an extremely high recovery rate, downtime is short, and there will not be any serious disruption in operations. Great cyber resilience also means that despite an incident, the business functions can carry on with minimum disturbance.
How Does a Cyber Security Assessment Help in Protecting Data?
Cyber security testing is very instrumental in data security because it determines weak points where breaches might occur. They assist companies in verifying that data encryption, safe data storage habits, user authentication, and access controls are sufficient to avoid attacks. The assessments serve to guard sensitive customer and business information and minimize the risk of expensive hacking or breach of data enhancing the relationship and general confidence between customers and all stakeholders.
Cyber Security Assessment Tools and Software
Frequently Asked Questions
Everything you need to know about Cyber Security Assessment
We're Here to Secure Your
Hard Work
Protect your system from cyber attacks by utilizing our comprehensive range of services. Safeguard your data and network infrastructure with our advanced security measures, tailored to meet your specific needs. With our expertise and cutting-edge technology, you can rest assured that your system is fortified against any potential threats. Don't leave your security to chance – trust our proven solutions to keep your system safe and secure.
Share this :